Table of Contents
HoverFly
CA LISA
ServiceVirtualization tool. Like CA LISA: http://www.itko.com/solutions/service_virtualization.jsp
Microservices and “HoverFly” https://www.linkedin.com/pulse/hoverfly-virtualizing-microservices-testing-eldad-uzman
Hoverfly
Download http://hoverfly.readthedocs.io/en/latest/pages/introduction/downloadinstallation.html
Documentation: https://media.readthedocs.org/pdf/hoverfly/v0.10.2/hoverfly.pdf
Repository: https://github.com/SpectoLabs/hoverfly Releases: https://github.com/SpectoLabs/hoverfly/releases/
Tutorials: http://hoverfly.readthedocs.io/en/latest/pages/tutorials/basic/basic.html#
Starting hoverfly
# start hoverfly \ -ap 8006 \ -pp 8005 \ -username "admin" \ -password "pass" \ -listen-on-host 0.0.0.0 \ -logs-file "/tmp/hoverfly.log" # start on windows .\hoverfly ` -ap 8888 ` -pp 8005 ` -username "admin" ` -password "pass" ` -listen-on-host 0.0.0.0 ` -logs-file "/tmp/hoverfly.log"
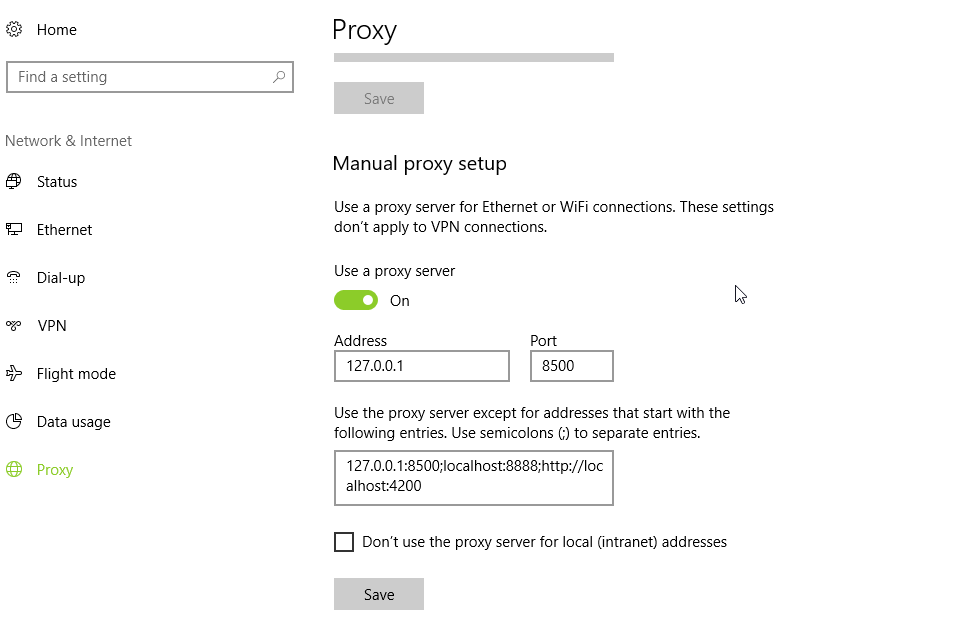
Enable proxy
To enable the proxy - you can proxy everything. You will just have to allow the traffic to the hoverfly running on port 8888, and to the frontend running on port 8500 or 4200.
Depending on the way, you started it- via a jar or via a “ng start”
Recording the traffic
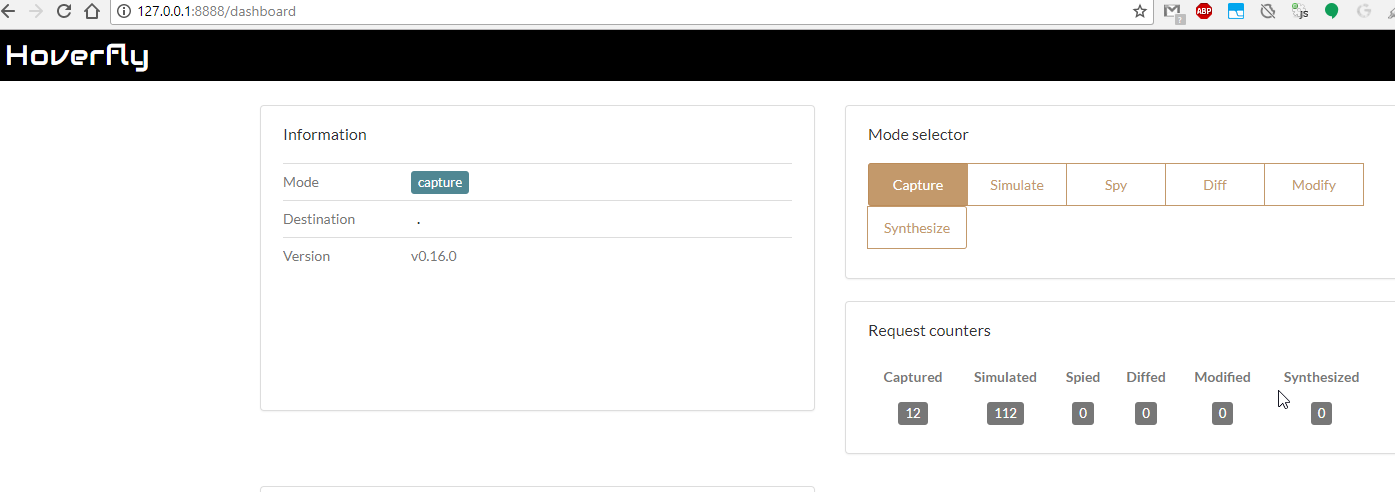
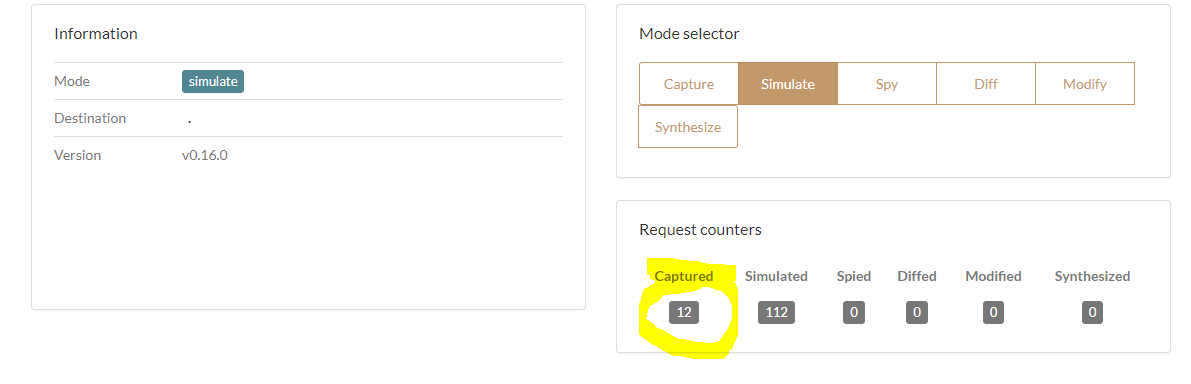
Set the hoverfly into the “Capture mode”.
And record the traffic, e.g. by navigating the REST api URLs manually.
Then export the strategy.json
hoverctl export simulation.json
Congratulation! You are now independent from the backend and may test the frontend - independently from backend.
By just importing the recorded actions
hoverctl import simulation.json
how do I configure Ubuntu OS, to route all HTTP and HTTPS traffic via a HTTP proxy as a gateway?
Ideally one would not want to configure the application under test.
So we search for a proxification method, allowing to redirect HTTP, HTTPS traffic via a proxy transparently to the application.
Here https://github.com/SpectoLabs/hoverfly/issues/774 the tool *proxychains* is recommended.
@Deprecated https://github.com/haad/proxychains
Replacement https://github.com/rofl0r/proxychains-ng
Install proxychains
sudo apt update sudo apt install proxychains4
Configure the proxychain
sudo vim /etc/proxychains.conf
# proxychains.conf VER 3.1 # # HTTP, SOCKS4, SOCKS5 tunneling proxifier with DNS. # # The option below identifies how the ProxyList is treated. # only one option should be uncommented at time, # otherwise the last appearing option will be accepted # #dynamic_chain # # Dynamic - Each connection will be done via chained proxies # all proxies chained in the order as they appear in the list # at least one proxy must be online to play in chain # (dead proxies are skipped) # otherwise EINTR is returned to the app # strict_chain # # Strict - Each connection will be done via chained proxies # all proxies chained in the order as they appear in the list # all proxies must be online to play in chain # otherwise EINTR is returned to the app # #random_chain # # Random - Each connection will be done via random proxy # (or proxy chain, see chain_len) from the list. # this option is good to test your IDS :) # Make sense only if random_chain #chain_len = 2 # Quiet mode (no output from library) #quiet_mode # Proxy DNS requests - no leak for DNS data proxy_dns # Some timeouts in milliseconds tcp_read_time_out 15000 tcp_connect_time_out 8000 # ProxyList format # type host port [user pass] # (values separated by 'tab' or 'blank') # # # Examples: # # socks5 192.168.67.78 1080 lamer secret # http 192.168.89.3 8080 justu hidden # socks4 192.168.1.49 1080 # http 192.168.39.93 8080 # # # proxy types: http, socks4, socks5 # ( auth types supported: "basic"-http "user/pass"-socks ) # [ProxyList] # add proxy here ... # meanwile # defaults set to "tor" http 127.0.0.1 8005
*note* :
“proxy_dns” is key here, otherwise the certificates of “hoverfly” wont be accepted.
Make the OS trust the hoverfly CA certificate
Add it to the trusted certificates https://ubuntu.com/server/docs/security-trust-store
# get the hoverfly cert wget https://raw.githubusercontent.com/SpectoLabs/hoverfly/master/core/cert.pem -O /tmp/hovercert_ca.crt sudo apt-get install -y ca-certificates sudo cp /tmp/hovercert_ca.crt /usr/local/share/ca-certificates sudo update-ca-certificates
Call some URL with proxy in the middle
Now you can make “proxychains” curl a “https” URL and it works with the proxy inbetween.
proxychains curl -iv https://google.com [proxychains] config file found: /etc/proxychains.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.14 * Trying 224.0.0.1:443... * TCP_NODELAY set [proxychains] Strict chain ... 127.0.0.1:8005 ... google.com:443 ... OK * Connected to google.com (127.0.0.1) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: /etc/ssl/certs/ca-certificates.crt CApath: /etc/ssl/certs * TLSv1.3 (OUT), TLS handshake, Client hello (1): * TLSv1.3 (IN), TLS handshake, Server hello (2): * TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8): * TLSv1.3 (IN), TLS handshake, Certificate (11): * TLSv1.3 (IN), TLS handshake, CERT verify (15): * TLSv1.3 (IN), TLS handshake, Finished (20): * TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.3 (OUT), TLS handshake, Finished (20): * SSL connection using TLSv1.3 / TLS_AES_128_GCM_SHA256 * ALPN, server did not agree to a protocol * Server certificate: * subject: O=GoProxy untrusted MITM proxy Inc; CN=google.com * start date: Jan 1 00:00:00 1970 GMT * expire date: Dec 31 00:00:00 2049 GMT * subjectAltName: host "google.com" matched cert's "google.com" * issuer: O=Hoverfly Authority; CN=hoverfly.proxy * SSL certificate verify ok. > GET / HTTP/1.1 > Host: google.com > User-Agent: curl/7.68.0 > Accept: */* > * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * Mark bundle as not supporting multiuse < HTTP/1.1 301 Moved Permanently HTTP/1.1 301 Moved Permanently < Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000 Alt-Svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000 < Cache-Control: private, max-age=2592000 Cache-Control: private, max-age=2592000 < Connection: close Connection: close < Content-Security-Policy-Report-Only: object-src 'none';base-uri 'self';script-src 'nonce-iSN12G9UbZBSihIw67Ct5w' 'strict-dynamic' 'report-sample' 'unsafe-eval' 'unsafe-inline' https: http:;report-uri https://csp.withgoogle.com/csp/gws/other-hp Content-Security-Policy-Report-Only: object-src 'none';base-uri 'self';script-src 'nonce-iSN12G9UbZBSihIw67Ct5w' 'strict-dynamic' 'report-sample' 'unsafe-eval' 'unsafe-inline' https: http:;report-uri https://csp.withgoogle.com/csp/gws/other-hp < Content-Type: text/html; charset=UTF-8 Content-Type: text/html; charset=UTF-8 < Date: Fri, 23 Jun 2023 06:30:08 GMT Date: Fri, 23 Jun 2023 06:30:08 GMT < Expires: Fri, 23 Jun 2023 06:30:08 GMT Expires: Fri, 23 Jun 2023 06:30:08 GMT < Hoverfly: Was-Here Hoverfly: Was-Here < Location: https://www.google.com/ Location: https://www.google.com/ < P3p: CP="This is not a P3P policy! See g.co/p3phelp for more info." P3p: CP="This is not a P3P policy! See g.co/p3phelp for more info." < Server: gws Server: gws < Set-Cookie: CONSENT=PENDING+692; expires=Sun, 22-Jun-2025 06:30:08 GMT; path=/; domain=.google.com; Secure Set-Cookie: CONSENT=PENDING+692; expires=Sun, 22-Jun-2025 06:30:08 GMT; path=/; domain=.google.com; Secure < Transfer-Encoding: chunked Transfer-Encoding: chunked < X-Frame-Options: SAMEORIGIN X-Frame-Options: SAMEORIGIN < X-Xss-Protection: 0 X-Xss-Protection: 0 < <HTML><HEAD><meta http-equiv="content-type" content="text/html;charset=utf-8"> <TITLE>301 Moved</TITLE></HEAD><BODY> <H1>301 Moved</H1> The document has moved <A HREF="https://www.google.com/">here</A>. </BODY></HTML> * Closing connection 0 * TLSv1.3 (OUT), TLS alert, close notify (256):