Table of Contents
Netflix
Open VPN Proxy
- The cloud formation proxy, for the OpenVPN deployment.
- For the deployment of an OpenVPN Server in US East (N. Virginia)
- To deploy the instance in another region - you have to replace InstanceAMI ami-f6eed4e0 by another AMI. Find the right AMI under “Manual Deployment ” on the marketplace: https://aws.amazon.com/marketplace/pp/B00MI40CAE/ref=mkt_wir_openvpn_byol
---
AWSTemplateFormatVersion: "2010-09-09"
Description: Establishes an OpenVPN server in a public subnet within a new VPC
Parameters:
InstanceAMI:
Description: OpenVPN AMI
Type: String
Default: ami-f6eed4e0
InstanceTypeM:
Description: OpenVPN Instance Type
Type: String
AllowedValues:
- t2.nano
- t2.micro
- t2.small
- t2.medium
- t2.large
Default: t2.micro
KeyName:
Description: SSH Key Name
Type: AWS::EC2::KeyPair::KeyName
AdminPassword:
Description: OpenVPN Admin Password
Type: String
NoEcho: true
MinLength: 8
MaxLength: 32
ConstraintDescription: Must be at least 8 chars long
RouteAllTraffic:
Description: Should all local traffic go over VPN when connected?
Type: Number
AllowedValues:
- 0
- 1
Default: 1
UseVPNDNS:
Description: Should client use VPN supplied DNS when connected?
Type: Number
AllowedValues:
- 0
- 1
Default: 1
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: "10.0.0.0/16"
Tags:
- Key: Name
Value: OpenVPN
PublicSubnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: "10.0.0.0/24"
Tags:
- Key: Name
Value: OpenVPN Public Subnet
InternetGateway:
Type: AWS::EC2::InternetGateway
AttachGateway:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
RouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Route:
Type: AWS::EC2::Route
DependsOn: AttachGateway
Properties:
RouteTableId: !Ref RouteTable
DestinationCidrBlock: "0.0.0.0/0"
GatewayId: !Ref InternetGateway
SubnetRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicSubnet
RouteTableId: !Ref RouteTable
IPAddress:
Type: AWS::EC2::EIP
Properties:
Domain: "vpc"
SecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
VpcId: !Ref VPC
GroupDescription: Security group for OpenVPN Server
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 443
ToPort: 443
CidrIp: "0.0.0.0/0"
- IpProtocol: tcp
FromPort: 943
ToPort: 943
CidrIp: "0.0.0.0/0"
- IpProtocol: udp
FromPort: 1194
ToPort: 1194
CidrIp: "0.0.0.0/0"
OpenVPNInstance:
Type: AWS::EC2::Instance
DependsOn: IPAddress
Properties:
ImageId: !Ref InstanceAMI
InstanceType: !Ref InstanceTypeM
KeyName: !Ref KeyName
SecurityGroupIds:
- !Ref SecurityGroup
SubnetId: !Ref PublicSubnet
Tags:
- Key: Name
Value: OpenVPN Instance
UserData:
Fn::Base64: !Sub |
public_hostname=${IPAddress}
admin_user=openvpn
admin_pw=${AdminPassword}
reroute_gw=${RouteAllTraffic}
reroute_dns=${UseVPNDNS}
IPAssociaton:
Type: AWS::EC2::EIPAssociation
DependsOn: OpenVPNInstance
Properties:
AllocationId: !GetAtt IPAddress.AllocationId
InstanceId: !Ref OpenVPNInstance
Outputs:
OpenVPNLogin:
Description: OpenVPN Login username
Value: openvpn
OpenVPNServerAdminURL:
Description: OpenVPN Administration URL
Value: !Sub https://${IPAddress}:943/admin
OpenVPNServerURL:
Description: OpenVPN Server URL
Value: !Sub https://${IPAddress}
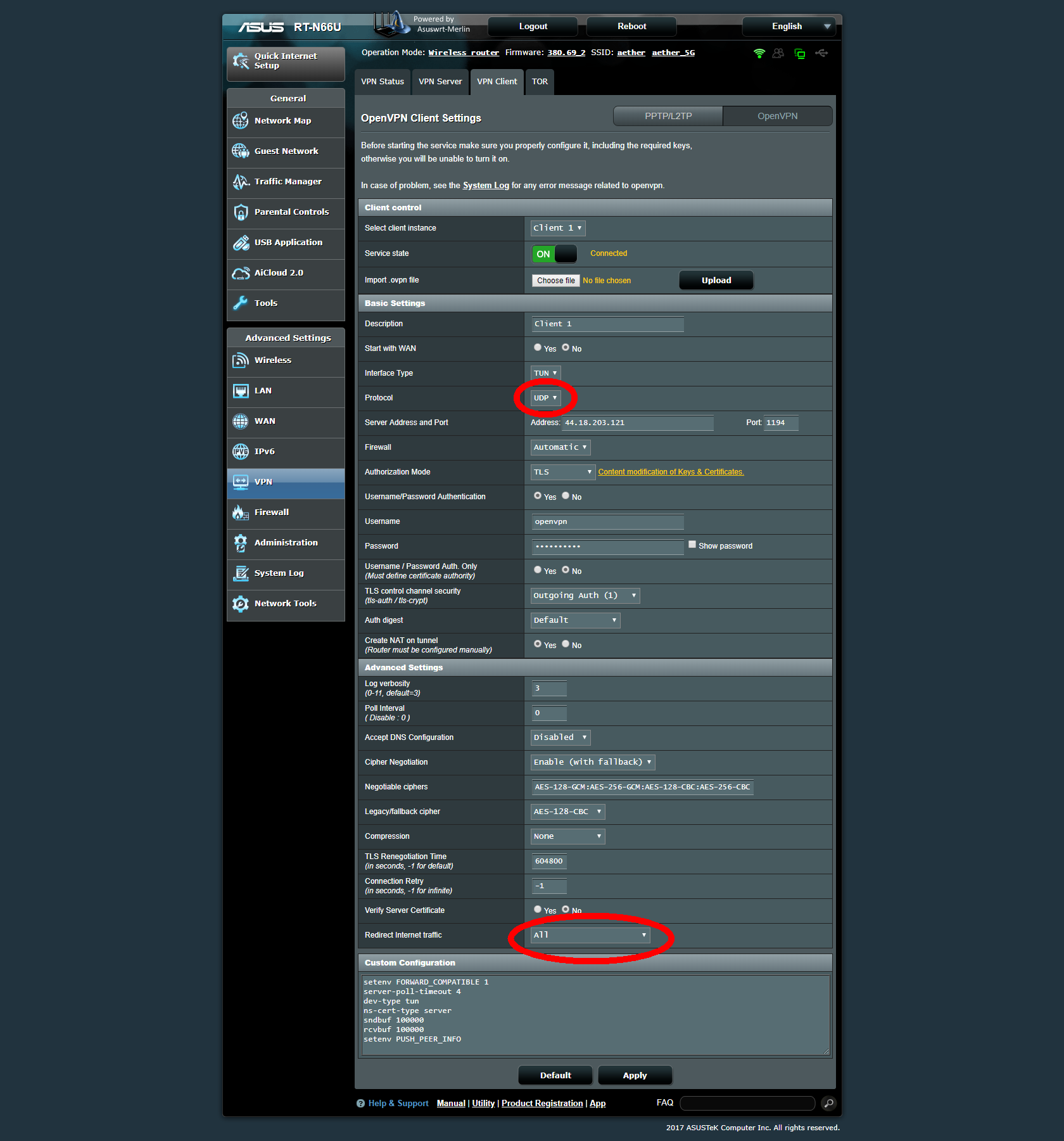
Router Asus RT-N66U
To enable VPN tunneling on your Asus RT-N66U
- Install “Merlin Firmware” from https://asuswrt.lostrealm.ca/ to enable VPN Client function on your router
- Download the client.ovpn file from your OpenVPN server and upload it to the router
- Check that UDP is marked as the protocol.
Only UDP is allowed by the firewall and accepted by the OpenVPN server deployed above.

Config VPN client
In Merlin-WRT the client configuration is located in
/etc/openvpn/client1/config.ovpn
Here the ip may be modified:
# Automatically generated configuration daemon client dev tun11 proto udp remote 44.18.203.121 1194 resolv-retry infinite nobind persist-key persist-tun compress ncp-ciphers AES-128-GCM:AES-256-GCM:AES-128-CBC:AES-256-CBC cipher AES-128-CBC script-security 2 route-delay 2 route-up vpnrouting.sh route-pre-down vpnrouting.sh verb 3 reneg-sec 604800 tls-auth static.key 1 ca ca.crt cert client.crt key client.key auth-user-pass up status-version 2 status status 5 # Custom Configuration setenv FORWARD_COMPATIBLE 1 server-poll-timeout 4 dev-type tun ns-cert-type server sndbuf 100000 rcvbuf 100000